Follow the steps in the order listed
Steps to enable the download monitoring
1. Click on the S3 bucket to view objects
2. Click on Management Tab inside the bucket
3. Click on Metrics
4. Click on Edit icon(small Pencil icon) under the metrics filters
5. Enable Checkbox on the feature "Request metrics(10)"
Note: This will take time to populate new monitoring data into the cloudwatch, This is also a paid feature
Steps to create 2 Topics
1. Open Amazon SNS
2. Click on Topics
3. Create Topic with a name: Topic-Restrict-Bucket
4. Create Topic with a name: Topic-Normalise-Bucket-Condition
Steps to create 2 Lambda Functions
import json
import boto3
def lambda_handler(event, context):
client = boto3.client('s3')
snsjson=event["Records"][0]["Sns"]
messagejson=json.loads(snsjson["Message"])
bucket_name=messagejson["Trigger"]["Dimensions"][0]["value"]
policy = client.get_bucket_policy(Bucket=bucket_name)
jsond=json.loads(policy["Policy"])
jsond["Statement"][0]["Effect"] = "Deny"
response = client.put_bucket_policy(Bucket=bucket_name, Policy=str(json.dumps(jsond)),)
import json
import boto3
def lambda_handler(event, context):
client = boto3.client('s3')
snsjson=event["Records"][0]["Sns"]
messagejson=json.loads(snsjson["Message"])
bucket_name=messagejson["Trigger"]["Dimensions"][0]["value"]
policy = client.get_bucket_policy(Bucket=bucket_name)
jsond=json.loads(policy["Policy"])
jsond["Statement"][0]["Effect"] = "Allow"
response = client.put_bucket_policy(Bucket=bucket_name, Policy=str(json.dumps(jsond)),)
Steps for Adding 2 subscription to the topic
1. Go to Amazon SNS
2. Navigate to Subscriptions
3. Click on Create Subscriptions
4.
5. Create Subscription
6. Do steps 3 to 5 withe the following changes
The above will provide ability to edit the bucket policy automatically when triggered in a situation of download threshold breach.
The above can be used by any bucket having the same type of policy.
Task
Major
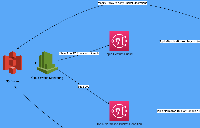
Cloudwatch allows monitoring of NetworkIn and NetworkOut for EC2 instances. Based on that we can implement a lambda function that if triggered based on a threshold breach and would halt the http access by temporarily adding a restriction on the security group and starting a timer. on timer completion we can undo the changes on the security group. Looking into some more options